Firewall is a device that protects data on systems and the computer system themselves. Firewall provides a controll point of entry into and out of computer system (internal network). Computer system may a very large investment for a company. Firewall help to minimize the chance of needed repairs for an intrusive attack from outside (such as Internet). Firewall is a safegruad which protect (Zalenski, 2002):
- Data integrity - Data needs to be protected from any unwarranted changed
- Availability - Data needs to be accessible when needed
- Secrecy - Data privacy needs to be secured when applicable
Firewall Vendors:
- Check Point - http://www.checkpoint.com, provides integrated appliance solutions (Security Gateways) for both hardware and software
- SonicWALL - http://www.sonicwall.com, provides both hardware and software firewall products
- Juniper Networks - http://www.juniper.net, provides both hardware and software integrating firewall called NetScreen.
2. Find out if your university or workplace has a backup policy in place. Is it followed and enforced?
My company has the backup policy:
- Critical data should be backed up
- Backup data should be stored at a location that is physically different from its original creation and usage location
- The ability to retrieve and restore backup data should produce successful results. The verification through restoration from backed-up data, should be performed on a regular basis
- Procedures for backing up critical data and testing of the procedures should be documented.
- We backup application's data, user's data and users' e-mail daily
- Write down the daily backup status in the log book
- Store the backup tapes in China's office
- Restore the backup files from tape monthly for verification
I search the 'virus writing kit' in Yahoo. The result of it:
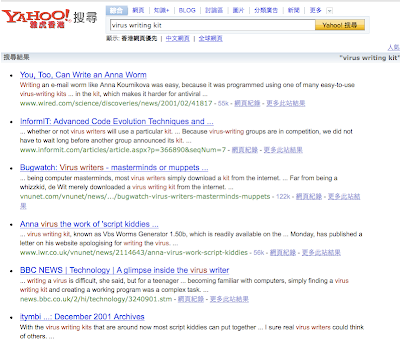
There are many documents in the internet talking about virus writing kits. They said that the virus writing are easy be downloaded from the Internet like (Szor, 2005):
- VCS (Virus Construction Set) - the first virus generator written in 1990.
- GenVir - released as a shareware in France by J. Struss in 1990-1991.
- VCL (Virus Creation Laboratory) - was written in US in 1992.
- PS-MPC (Phalcon-Skism Mass-Produced Code Gemnerator) - was created in 1992 in US by Dark Angel.
- NGVCK (Next Generation Virus Creation Kit) - introduced in 2001 by SnakeByte
- Amateurs - over 150 kits and code mutators are available, in 1996 such tools become extremely popular

Reference
- Zalenski, R. (2002), Firewal technologies, Potentials, IEEE, 24-29.
- Szor, P. (2005), Advanced code evolution techniques and computer virus generator kits, informIT network, Retreived at https://www.informit.com/articles/article.aspx?p=366890&seqNum=7 on 27th April, 2009.


No comments:
Post a Comment